A Risk level is calculated by adding together the probabilities of all problem situations and the financial harm that results from them. Provide information for risk analysis and quality improvement.
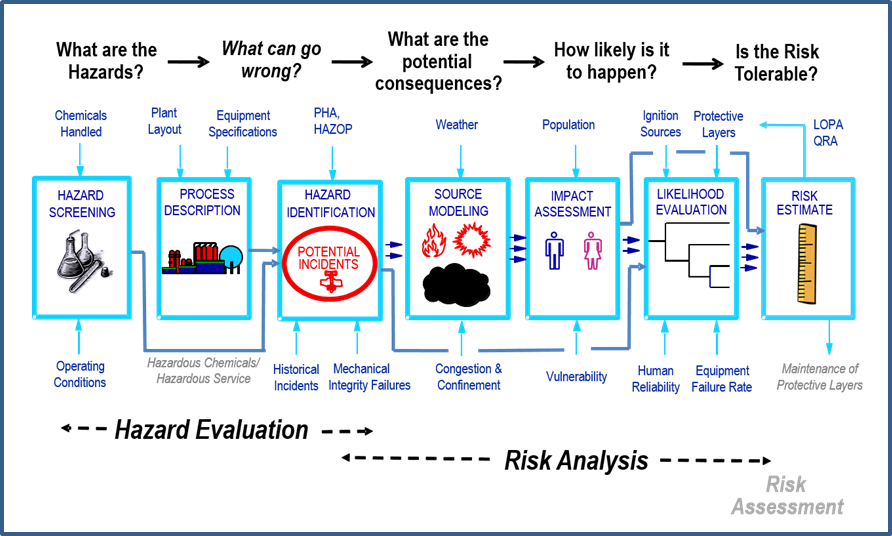
Risk Analysis Screening Tool Rast And Chemical Hazard Engineering Fundamentals Chef Aiche
None of the above 52 All of the following are phases of systems analysis except 1.
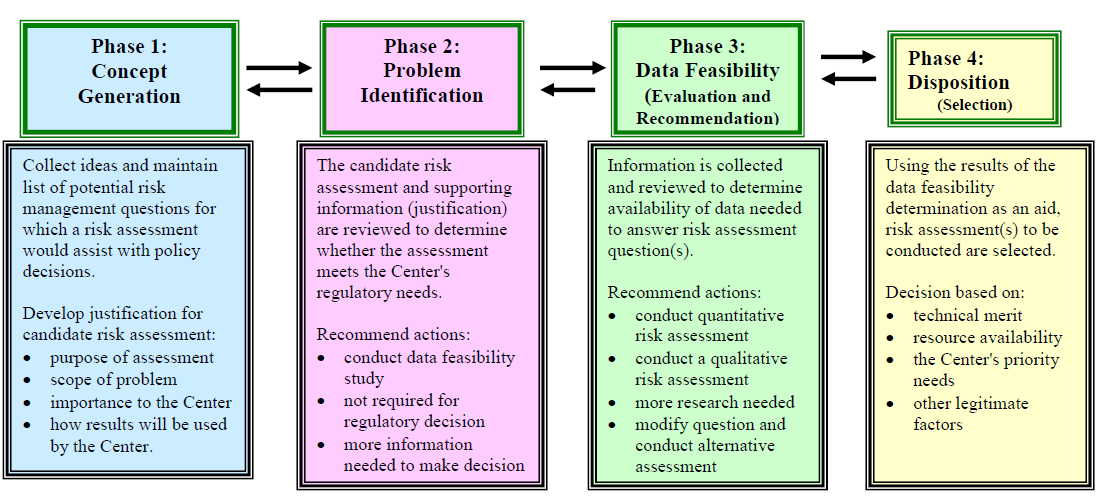
. A risk-analysis method that uses mathematical formulas and numbers to assist in ranking risk severity. Include estimates of current structure contents and function losses primarily for potentially affected historical buildings C. Unknown NOT USER DOMAIN LAN DOMAIN 3.
Group of answer choices Risk analysis is a methodapproach to evaluate the potential loss of IT assets given a disaster incident. The Risk Analysis implementation specification requires covered entities to. Risk is the probability and magnitude of harm resulting from exposure to hazards.
To identify standards inconsistencies in the code. A process used by the person or the persons assigned risk management functions to determine the potential severity of the loss from an identified risk the probability that the loss will. Which of the following is NOT part of system testing.
The __________ is the proportion of an assets value that is likely to be destroyed by a particular risk. Organizations are struggling with risks on multiple fronts including cybersecurity liability investment and more. IT risk analysis focuses on the risks that both internal and external threats pose to the availability confidentiality and integrity of your data.
Risk analysis is a. A major problem that requires formal escalation. Risk is the potential for exposure and is primarily related toxicity.
Which of the following BEST describes why risk assessment can be viewed as the foundation of the audit function. Decision analysis phase 2. QUESTION 1 Which of the following best define Risk analysis.
The design specification for the system wrongly states speeds in kmh. It is used to determine the costbenefit of a control. Identifying and acknowledging threats and opportunities.
To identify spelling mistakes in a requirements specification. Minimising threats and maximising opportunities. System development documentation can be broken down into four categories of documentation.
In which of the IT domains is a hub considered a major component of risk. The administrative safeguards of the HIPAA Security Rule require all HIPAA-covered entities to conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality integrity and availability of electronic protected health information. Risk assessment provides a framework for allocating limited resources to achieve maximum benefits and value derived from the audit process.
How does risk management impact an organization. While the Security Rule doesnt set a required timeline HHS recommends organizations conduct another risk analysis whenever your company implements or plans. Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality integrity and availability of electronic protected health information held by the covered entity In general a risk analysis can be viewed as.
164308 u 1 ii. Risk involves the quantitative assessment of exposure. You have identified the risk and conducted a risk analysis on the possible failure of the fuel pump.
Risk analysis allows us to identify areas of possible business improvement. Affects the survivability 4. Which of the following statements best describes risk.
Project risk management is best described as. Planning responses to threats. The NIST HIPAA Security Toolkit Application developed by the National Institute of Standards and Technology NIST is intended to help organizations better understand the requirements of the HIPAA Security Rule implement those requirements and assess those implementations in their operational environment.
The PSM has asked you the LCL to assess one situation and identify the sustainment risks associated. Which of the following BEST describes the difference between an inspection and a. Which of the following best describes risk assessment.
During risk analysis a. B Risk level is estimated by multiplying the likelihood of a threat to the system by the chance that the threat will occur and will result in financial damage c Risk level is determined by a combination of the probability of an undesirable event and the. Risk analysis is a process that is conducted to simply impress auditors.
Which of the following is the BEST description of risk. As a result of risk analysis more testing is being directed to those areas of the system under. Which of the following best describes risk analsysis.
In which category of documentation are you likely to find data dictionary entries data flow diagrams object models screen layouts source documents and the systems request that initiated the project. Which of the following best describes quantitative risk analysis. Guidance on Risk Analysis.
Which of the following BEST describes what you should include in the updated risk assessment. Risk analysis or risk assessment is the first step in the risk management process. 1 The Strike Talon UCAS has just completed its IOTE testing and there were some program issues that may create sustainment risks.
Risk assessment determines the potential frequency of the occurrence of a problem and potential damage if the problem were to occur. Periodic Review and Updates to the Risk Assessment Its important the risk analysis process is ongoing one requirement includes conducting a risk analysis on a regular basis. Risk assessment enables flexibility in approaching audits.
Risk almost always involves a high degree of uncertainty. Update the loss estimate to reflect changes to the hazard profile andor to the inventory of structures B. The probability of loss of a valued resource 2.
Your next step is risk handling. Rapid architected analysis 4. Include an estimate of the potential.
Managing responses to threats. 51 A model-driven analysis approach that focuses on the structure of stored data in a system rather than on processes is 1. Which of the following is not a technique for.
Which of the following BEST describes how value is added by maintaining traceability. The HIPAA Risk Analysis. Which one of the following best describes a project issue.
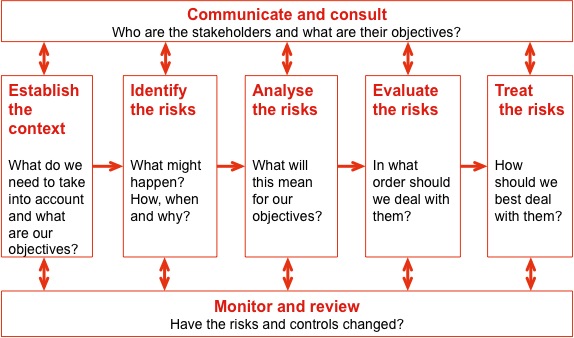
Risk Assessment And Risk Treatment Broadleaf

Initiation And Conduct Of All Major Risk Assessments Within A Risk Analysis Framework Fda
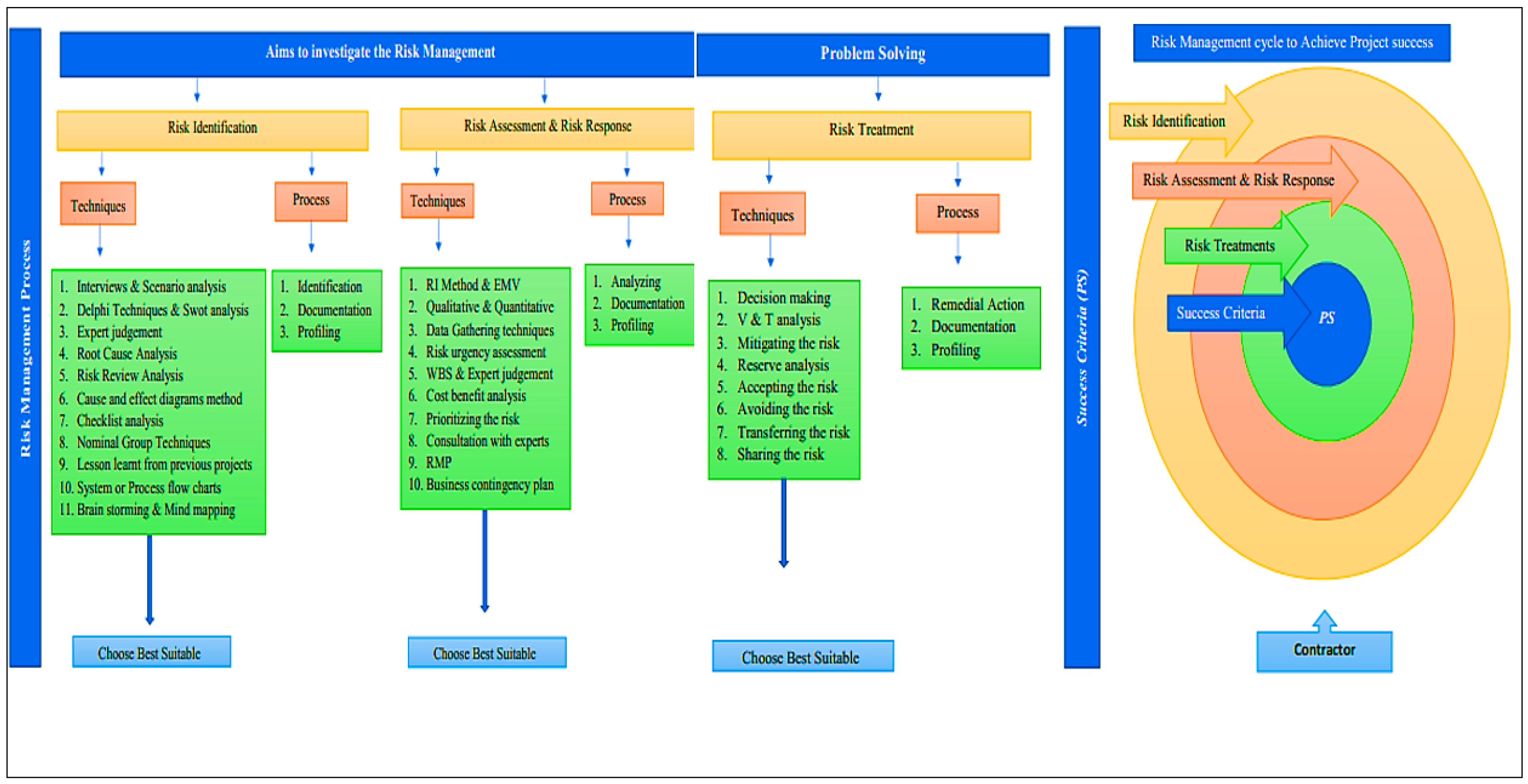
Risks Free Full Text An Innovative Framework For Risk Management In Construction Projects In Developing Countries Evidence From Pakistan Html
0 Comments